When I read about the use of Tiller in the article on SAP AI vulnerabilities, I was a bit surprised. The article came out around three and a half years after Helm v2 - which includes Tiller - reached its end of life. It had been even longer since the last Helm v2 release.
Looking at the downloads of Tiller, I was surprised to find tens of thousands of downloads each week. The image blew is the downloads from the last 3 versions of Tiller. If I look beyond those 3 versions I can see even more downloads each week.
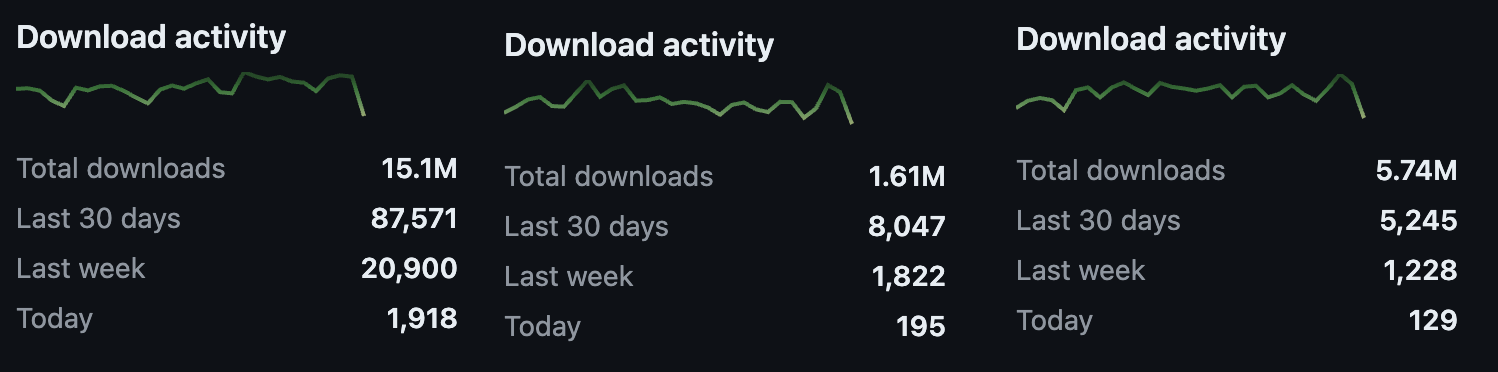
Helm v2 with Tiller still seems to get some decent use.
Some History
Helm v2.0.0, the first stable release with Tiller, was released in November of 2016. The stable minor version of Kubernetes at that time was 1.4. This is before Custom Resource Definitions (CRDs) and custom controllers existed. This was before RBAC in Kubernetes.
The Helm CLI communicated to a service named Tiller that ran in a cluster. Tiller was a precursor to modern custom controllers but without the security layers we are used to because they didn’t exist, yet. Tiller did the work to manage the instances of charts running in a cluster.
Helm v3 removed the need for a server side component. CRDs and custom controllers were considered but there were needs to use Helm in environments where the users didn’t have permission to installer CRDs or a custom controller. Since it wasn’t required, the cluster side component was dropped.
Please Stop Using Helm v2 and Tiller
Please stop using Helm v2 with Tiller.
Helm v2 was not designed for modern Kubernetes environments. The last updates were years ago. Just consider the security profile of an application that’s not had dependencies updated in years and those dependencies have had security vulnerabilities fixed. Helm v3 has also had vulnerabilities fixed.
There is a migration tool to aide in moving from Helm 2 to 3. The tool is archived now because it’s been so long since Helm v3 came out and Helm v2 hit its end of life. It should still work.