Disclaimer: I work for SUSE but I don’t work in the Linux business unit. I’m a consumer of the base container images like anyone else who uses them.
If you’re building a containerized applications you have a base container image at the bottom. That base container image can make a difference to your stack. Is it really large which impacts what you pass around on the network and cache? Is it secure or are there vulnerabilities that will affect your operations? If you’re a company and there is a problem, can you get support?
It’s easy to pick a base container image if you’re a small company (maybe a startup) or an open source project. It’s different if you’re in a regulated industry.
SUSE has been building and shipping Linux distros since 1992. They have been doing Linux for more than 30 years. Over those years they have gained a lot of experience in shipping Linux that those in regulated industries or those who need support tend to like.
The SUSE SLES Base Container Images provide a foundation to use for various base use cases. Before I dig into them, I want to share why you might be interested in looking at them in the first place.
Security
Security is important and it’s one of the things SUSE cares about. When Chainguard wrote the white paper “All About That Base Image” they looked at vulnerabilities in the most popular base images. Most of them had known vulnerabilities in the latest releases. Some of those vulnerabilities were long known ones that have not been fixed.
Like Alpine, SUSE is known to keep up to date and not have known CVEs in their latest bits. For example, here is trivy scanning the latest 1.19 Golang BCI:
$ trivy i registry.suse.com/bci/golang:1.19
2022-10-18T10:44:56.631-0400 INFO Vulnerability scanning is enabled
2022-10-18T10:44:56.631-0400 INFO Secret scanning is enabled
2022-10-18T10:44:56.631-0400 INFO If your scanning is slow, please try '--security-checks vuln' to disable secret scanning
2022-10-18T10:44:56.631-0400 INFO Please see also https://aquasecurity.github.io/trivy/v0.29.2/docs/secret/scanning/#recommendation for faster secret detection
2022-10-18T10:44:58.714-0400 INFO Detected OS: suse linux enterprise server
2022-10-18T10:44:58.714-0400 WARN This OS version is not on the EOL list: suse linux enterprise server 15.4
2022-10-18T10:44:58.714-0400 INFO Detecting SUSE vulnerabilities...
2022-10-18T10:44:58.715-0400 INFO Number of language-specific files: 0
2022-10-18T10:44:58.716-0400 WARN This OS version is no longer supported by the distribution: suse linux enterprise server 15.4
2022-10-18T10:44:58.716-0400 WARN The vulnerability detection may be insufficient because security updates are not provided
registry.suse.com/bci/golang:1.19 (suse linux enterprise server 15.4)
Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
Keeping up to date so there aren’t known CVEs isn’t the only thing SUSE does. SUSE regularly gets security certifications and puts considerable effort into security (e.g. a build system capable of producing common criteria 4+ builds).
The work they do around security and Linux keeps up with modern industry work. I’ve already written about how you can verify the BCI images with cosign including the SLSA provenance attestations.
Supportability
Sometimes you need support. Many businesses need and want it. SUSE provides support. There is support if you’re running the BCIs on SUSE Linux Enterprise Server (SLES) and if you’re running in some non-SLES locations. The following image is from the non-SLES support documentation:
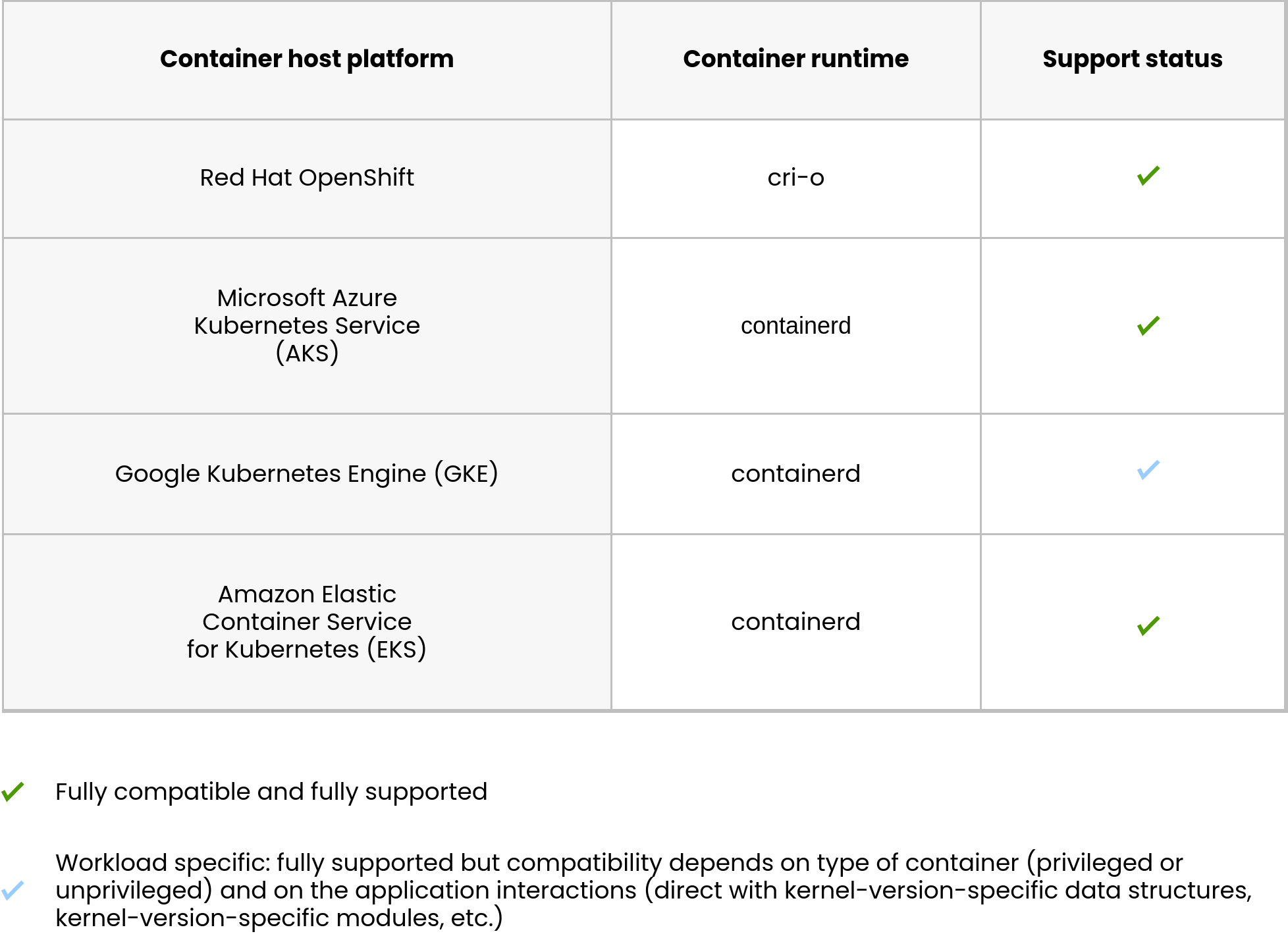
The BCIs are supported if you need that.
The Base Container Images
The SLES BCIs can be found at https://registry.suse.com/ and there are two types of images. There are those that are just the base system and those with common programming languages. This is useful if you need a runtime for your applications (e.g. nodejs) or a build environment (e.g. golang).
There are 4 different flavors of base image, depending on what you want in it. You can read about them in the container guide. The image below, from the docs, illustrates the differences in a simple manner:
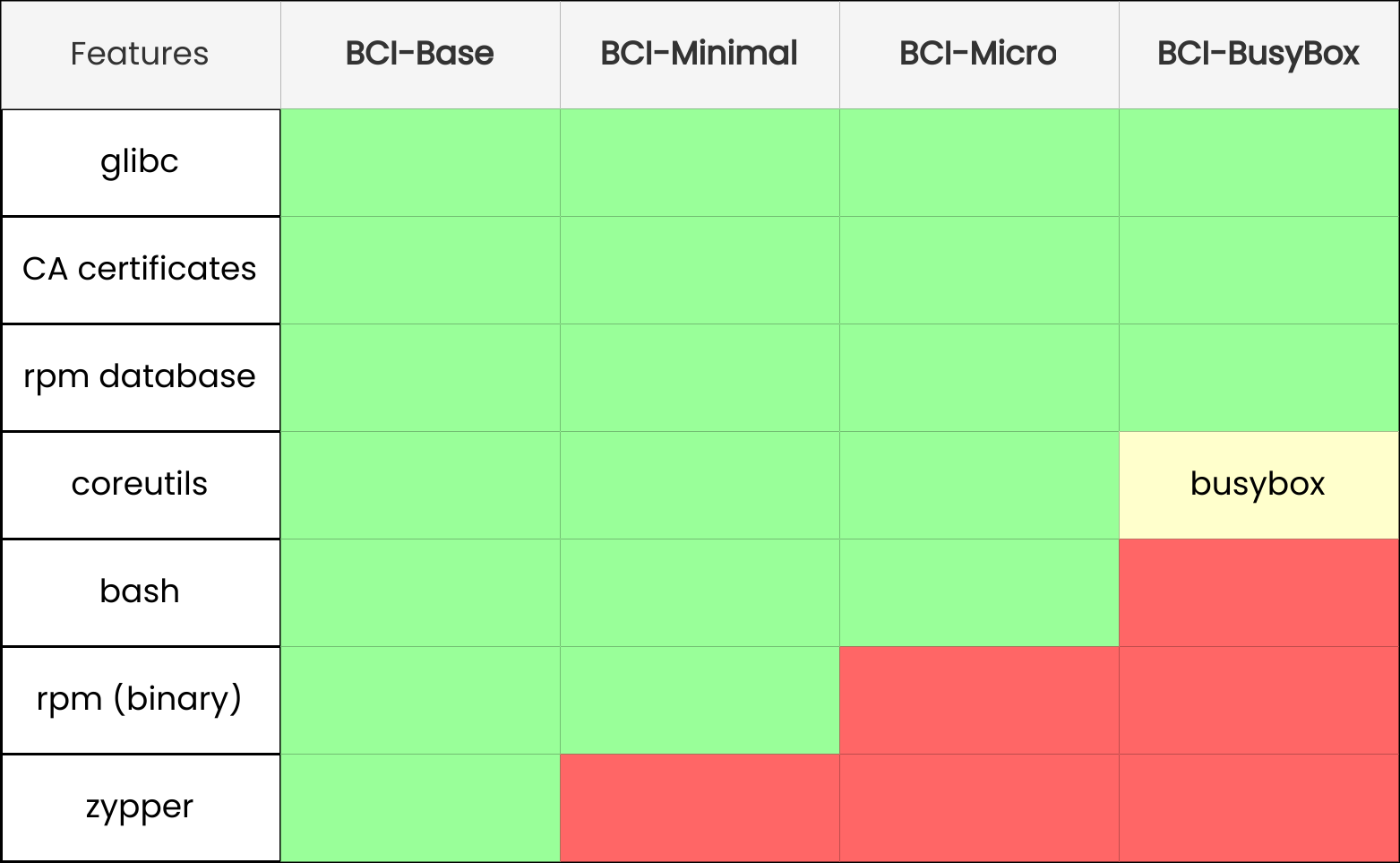
If you need an image with a language installed there are many to choose from. Go, nodejs, OpenJDK, Python, ASP.NET, and Rust. Note that you should look at the latest version being shipped to determine the version.
In addition to the Container Guide from SUSE, there’s additional documentation at https://opensource.suse.com/bci-docs/ which includes things like Building and Deploy Go Applications and Using With VS Code and Development Containers.
These images are like other base container images. They are what you’d expect and because of that they work with existing tools and systems.