Wouldn’t it be nice to know how up to date your Go dependencies are? In some languages there are tools that cover this. In some cases they go so far as to look at security reports to know where there are security issues in dependencies. A good example of this is David which provides insight into Nodejs projects.
I wanted something similar for Go. Without going to the same extent as David, at this point, I’d like to present Glide Report.
Review Your Go Dependencies
Glide Report, which is a plugin for Glide that currently works stand alone as well, will scan a codebase, look at repositories, gather information, and provide a report based on some rules.
Installing it, while currently in alpha is done with:
$ go get -u github.com/Masterminds/glide-report
You can run it from the root of a project with the command:
$ glide report
There is, currently, one flag of -no-color that can be used to remove color. This is useful when we want to copy from non-terminal environments. macOS example:
$ glide report -no-color | pbcopy
This will generate the report and copy the report, skipping the informational messages, to the clipboard.
The output, which you can see the beginning of below, will show the difference between direct and transitive dependencies.
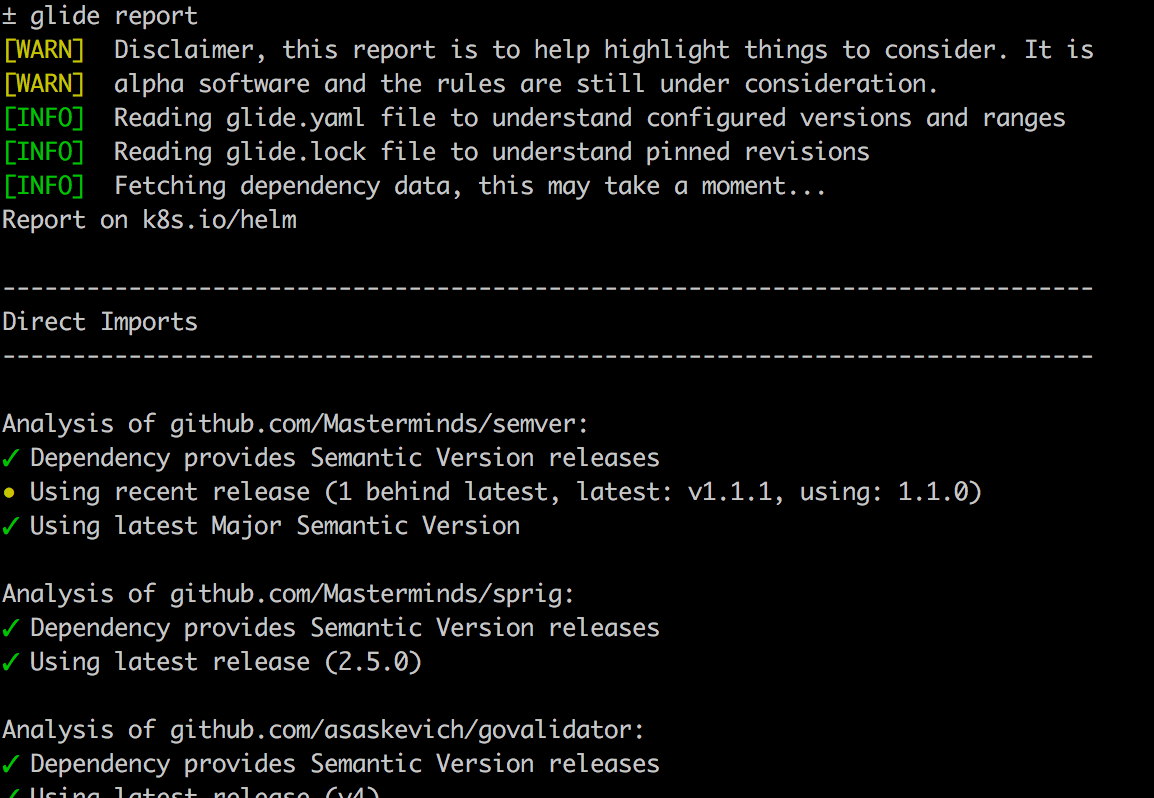
For examples you can see reports on Kubernetes and runC.
What If You Don’t Use Glide?
Glide has the ability to import from Godep, GPM, GOM, and GB. If your project is managed by one of them you use Glide Report. For example,
$ glide-report
This will detect missing glide.yaml and glide.lock files. It will then attempt to create them without making any alterations to your vendor/ folder. If that’s successful it will generate a report.
Just The Start
This is just the start. Being able to gain insight on our Go dependencies is useful and we can do more. If you’d like to contribute to Glide Report we’d love to have the contributions and feedback.
I also hope other tools come along in this space. There’s ample opportunity and I look forward to folks jumping on it.