Helm 4 Contributors, A Thank You
Helm v4 has been released after a year of development. There were a number of people who have contributed to Helm v4 and I want to say a big Thank You to them.
Helm v4 has been released after a year of development. There were a number of people who have contributed to Helm v4 and I want to say a big Thank You to them.

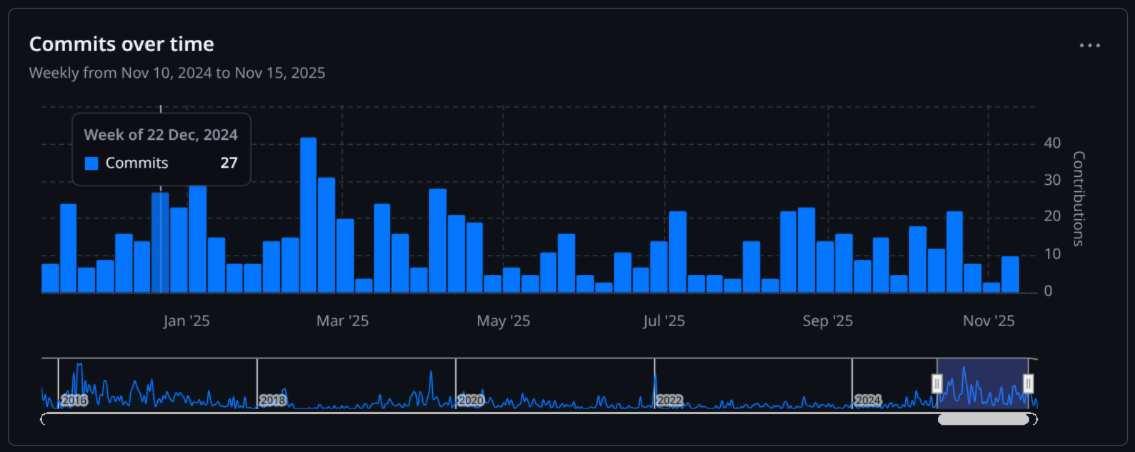
10 year ago I had my first commit against Helm. This is my 10 year anniversary.
commit b64d701023830999750c570a9224fa9dd3eb4a22
Author: Matt Farina <[email protected]>
Date: Wed Oct 28 13:52:21 2015 -0400
docs(README): add Go Report Card badge
I had been around the Kubernetes space for awhile and I have long known Matt Butcher, who had the first Helm commit. He showed me Helm and I found my niche to help contribute.

I’ve had the same terminal setup for years. Every year it gets some minor changes, usually in the form of additions. Over time, the whole setup has slowed down and fell into a state of being a mess rather than optimal or thought out. With the release of Ghostty, it seemed like a good time to rethink my whole setup.
I get asked a lot of questions that involve Semantic Versioning (a.k.a. SemVer). I also get told that something some piece of software does around it is wrong. Having spent far too much time dealing versions, this post tries to clear up some of the more common misconceptions.
When I read about the use of Tiller in the article on SAP AI vulnerabilities, I was a bit surprised. The article came out around three and a half years after Helm v2 - which includes Tiller - reached its end of life. It had been even longer since the last Helm v2 release.
Looking at the downloads of Tiller, I was surprised to find tens of thousands of downloads each week. The image blew is the downloads from the last 3 versions of Tiller. If I look beyond those 3 versions I can see even more downloads each week.
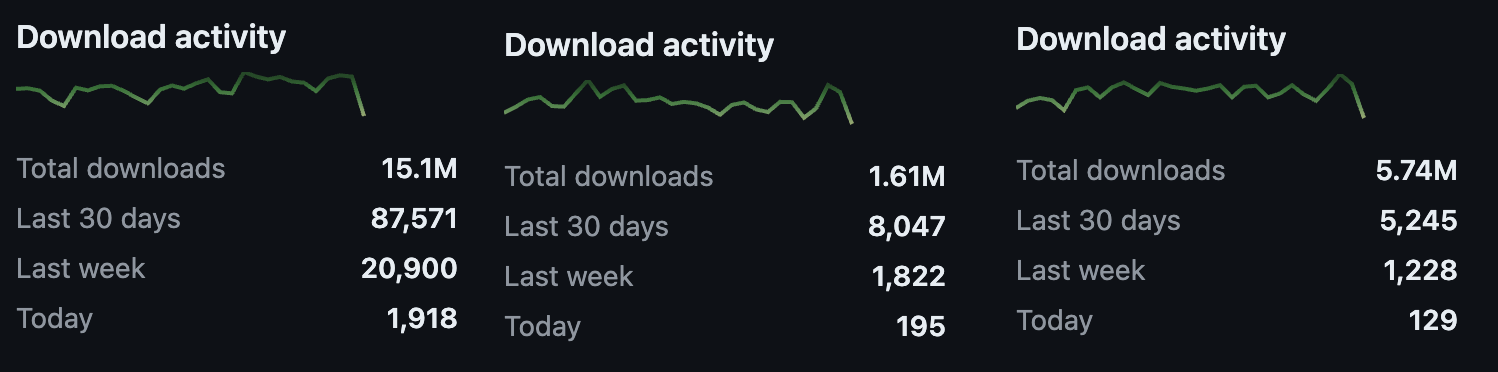
Helm v2 with Tiller still seems to get some decent use.